Instruction
1
Anonymous Tor network consists of so-called "nodes" (eng. nodes), as well to denote members of the network can be used the term "relay" (eng. relays). Each relay is a proxy server that can receive and send data. Any user configuring a Tor client can turn your PC into a node, i.e. the element of the chain network. Packet from the client to the server is not directly but through a chain consisting of three randomly selected nodes.
2
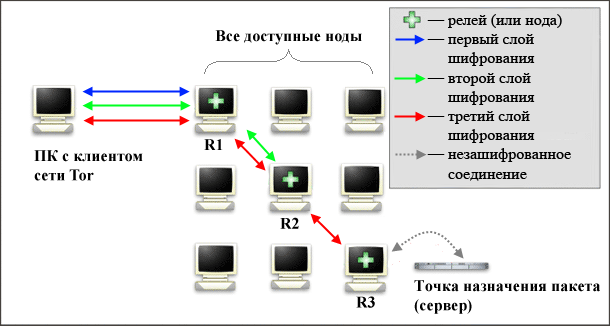
The approximate path, which passes each packet in the Tor network, schematically shown in figure:
3
When a user starts the client the Tor network, the latter connects to the Tor server and gets a list of all available nodes. From a large number of Rayleigh (5,000) randomly selected only three. Further data is transmitted on these three random nodes, and it is carried out consistently from the more "upper" relay to a more "bottom".
4
Before you send the packet to the first relay in the chain, the client-side is consistent with the encryption in this package: first to third nodes (red arrow), then for the second (green arrow) and finally, for the first (blue arrow).
5
When the first relay (R1) receives the packet, it decrypts the top-level (blue arrow). Thus, the relay receives data on how much further you want to send a package. Occurs the relay package, but with two layers of encryption instead of three. The second and third relay is the same way: each node receives the packet, decrypts the "a" layer and sends the packet on. The last (the third, R3) relay in the chain delivers the packet to the destination (server) unencrypted. The response from the server likewise passes through the same chain, but in the opposite direction.
6
This approach provides more assurance of anonymity than traditional proxies. Anonymity is achieved by the fact that the primary source of the package is hidden. Important is the fact that all nodes involved in the transfer, do not receive information about the contents of the package, but only the data about where it's encrypted message and to whom to pass it on.
To ensure anonymity in the Tor network is used as a symmetric encryption and asymmetric. Each layer uses both methods, which also distinguishes from Tor and other anonymizers.
To ensure anonymity in the Tor network is used as a symmetric encryption and asymmetric. Each layer uses both methods, which also distinguishes from Tor and other anonymizers.



