Instruction
1
Normally you need to view the active connections associated with the suspected infected computer of spyware. A properly configured computer must be connected to the network only when you open some page, or during the upgrade OS files and databases for the antivirus program. If the indicator of the network connection in the system tray and then "alive" itself and the computer, regardless of you, communicates with the Internet some information, you must find out the reasons of such network activity.
2
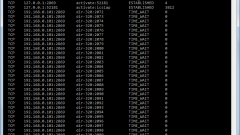
Open a command prompt, to do this, run: "start" - "All programs" - "Accessories" - "Command prompt". In the opened window enter the command netstat –aon and press Enter. You will see a list of all network connections that are active will be marked in the column "Status" as ESTABLISHED.
3
Note the column "Foreign address" it shows the ip with which were connected with your computer and connection port. Port 80, for example, typical web servers. But if you see some other port, this is cause for alarm. In this case, you need to find out what is installed on your computer, the application opens the connection.
4
Look at the last column, it lists the process identifiers (PID). Remember the ID of the suspicious process, then in the same window, type the command tasklist. Opens the list of running processes on your computer. In the first column indicates the names of the processes in the second – their IDs. Find the ID of a suspicious process, then to his left, view the name of the program to which it belongs.
5
What if the name of the process mean nothing to you? Type it into a search engine and you will get all the information about the process. If not, then it is very likely that you "caught" a new Trojan program, details of which have not yet hit the Internet and the database of the antivirus.
6
Pay attention to which port opens suspicious process – information about the open ports present in the column "Local address". Check the processes in the wait state connection – LISTENING. Behave backdoors – Trojans designed for concealed connection to the compromised computer. The server part of this program always "hangs" on some port and waits for connection from a computer hacker.
7
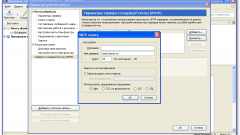
For full control of the connections, install the software BWMeter. This is one of the best programs of this class, it will allow you to see what address connects your computer, it is possible to record information in the log.